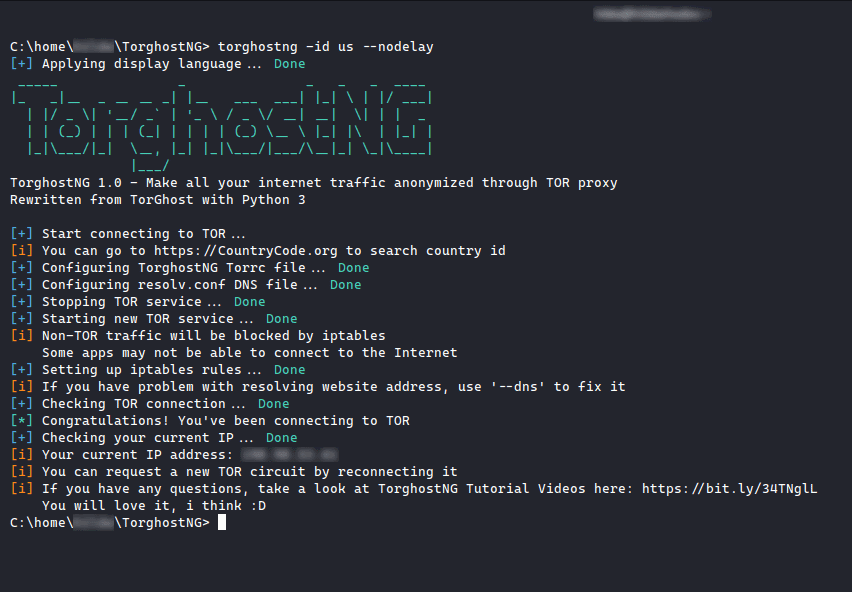
TorghostNG is a tool that make all your internet traffic anonymized with Tor network. TorghostNG is rewritten from TorGhost with Python 3.
TorghostNG was tested on:
- Kali Linux 2020a
- Manjaro
- ...
What's new in TorghostNG 1.2
- Fixed
update_commandsand others intorghostng.py - Changed a few things in
theme.py - Changed a few things in
install.py - Now you can change Tor circuit with
-r
Before you use TorghostNG
- For the goodness of Tor network, BitTorrent traffic will be blocked by iptables. Although you can bypass it with some tweaks with your torrent client 😥 It's difficult to completely block all torrent traffic.
- For security reason, TorghostNG is gonna disable IPv6 to prevent IPv6 leaks (it happened to me lmao).
Screenshots of Torghost (Version 1.0)
Connecting to Tor exitnode in a specific country:
torghostng -id COUNTRY IDChanging MAC address:
torghostng -m INTERFACEChecking IP address:
torghostng -cDisconnecting from Tor:
torghostng -xUninstalling TorghostNG:
python3 install.pyInstalling TorghostNG
TorghostNG installer currently supports:
- GNU/Linux distros that based on Arch Linux
- GNU/Linux distros that based on Debian/Ubuntu
- GNU/Linux distros that based on Fedora, CentOS, RHEL, openSUSE
- Solus OS
- Void Linux
- Anh the elder guy: Slackware
- (Too much package managers for one day :v)
To install TorghostNG, open your Terminal and enter these commands:
But with Slackware, you use
sudo python3 torghostng.py to run TorghostNG :vHelp
You can combine multiple choices at the same time, such as:
torghostng -s -m INTERFACE: Changing MAC address before connectingtorghostng -c -m INTERFACE: Checking IP address and changing MAC addresstorghostng -s -x: Connecting to Tor anh then stop :v- ...
I hope you will love it 😃
How to update TorghostNG
Open Terminal and type
sudo torghostng -u with sudo to update TorghostNG, but it will download new TorghostNG to /root, because you're running it as root. If you don't like that, you can type git pull -f and sudo python3 install.py.Notes before you use Tor
Tor can't help you completely anonymous, just almost:
- Tor's Biggest Threat – Correlation Attack
- Is Tor Broken? How the NSA Is Working to De-Anonymize You When Browsing the Deep Web
- Use Traffic Analysis to Defeat TOR
- ...
And please
- Don't spam or perform DoS attacks with Tor. It's not effective, you will only make Tor get hated and waste Tor's money.
- Don't torrent over Tor. If you want to keep anonymous while torrenting, use a no-logs VPN please.
Not anonymous: attack reveals BitTorrent users on Tor network
Changes log
Version 1.2
- Fixed
update_commandsand others intorghostng.py - Changed a few things in
theme.py - Changed a few things in
install.py - Now you can change Tor circuit with
-r
- Check your IPv6
- Change all "TOR" to "Tor"
- Block BitTorrent traffic
- Auto disable IPv6 before connecting to Tor
Contact to the coder
- Twitter: @SecureGF
- Github: @GitHackTools
- Website: GitHackTools 🙂
To-do lists:
- Block torrent, for you - Tor network (Done 😃)
- Connect to IPv6 relays (maybe?)
- GUI version
- Fix bug, improve TorghostNG (always)
And finally: You can help me by telling me if you find any bugs or issues. Thank you for using my tool 😊
Read more
- Pentest Tools Port Scanner
- Pentest Reporting Tools
- What Are Hacking Tools
- What Is Hacking Tools
- Hacker Tools For Ios
- Best Pentesting Tools 2018
- Pentest Tools Subdomain
- Growth Hacker Tools
- Hack Tools For Ubuntu
- Hacker Tools
- Black Hat Hacker Tools
- Hacker Hardware Tools
- Hack Tools 2019
- Pentest Tools Alternative
- Best Hacking Tools 2020
- Hacker Tools Online
- Top Pentest Tools
- Hack Tools
- Hack Tools For Pc
- Hacking Tools Github
- Hacking Tools Online
- Pentest Tools Apk
- Github Hacking Tools
- Hacking Tools 2020
- Pentest Box Tools Download
- What Is Hacking Tools
- Pentest Tools Apk
- Hack Tools For Windows
- Hacking Tools And Software
- Hacker Tools Free Download
- Hacker Tools Github
- Hacking Tools Free Download
- Pentest Tools Framework
- Hack Tools For Ubuntu
- Termux Hacking Tools 2019
- Hack Tools For Windows
- Pentest Tools Online
- Hacking Tools For Pc
- Pentest Tools Website
- Wifi Hacker Tools For Windows
- Pentest Tools Android
- Hacking Tools Online
- Hacker Tools Free Download
- Usb Pentest Tools
- Pentest Tools Website Vulnerability
- Pentest Tools Find Subdomains
- Hack Tools For Pc
- Pentest Tools Android
- Termux Hacking Tools 2019
- Hacker Tools 2019
- Pentest Tools Alternative
- Hacking Tools 2020
- Hak5 Tools
- Pentest Tools For Android
- Hacking Tools Mac
- Hacking Tools Pc
- Hacking Tools Online
- Pentest Tools Port Scanner
- Growth Hacker Tools
- Pentest Recon Tools
- Pentest Tools Alternative
- Hacking Tools For Windows 7
- Hacker Tools Apk Download
- Hack Tools
- Free Pentest Tools For Windows
- Hacker Hardware Tools
- Best Hacking Tools 2020
- Hacker Tool Kit
- Growth Hacker Tools
- Hacker Tool Kit
- Hacking Tools Kit
- Pentest Tools For Android
- Beginner Hacker Tools
- Pentest Tools Port Scanner
- Nsa Hacker Tools
- Hack Tools For Windows
- How To Hack
- Hacking Tools Online
- Hacker Tools Linux
- Top Pentest Tools
- Pentest Tools Github
- Hacking Tools For Kali Linux
- Hackrf Tools
- Hacking Tools For Pc
- Hacker Tools Software
- Pentest Tools Android
- Pentest Tools Alternative
- Hacking Tools Kit
- New Hack Tools
- Hack Tools Mac
- Hack Tools Github
- Pentest Tools Apk
- Hack Tools Online
- Tools 4 Hack
- Physical Pentest Tools
- Install Pentest Tools Ubuntu
- Hacker Tools Free Download
- Pentest Tools Tcp Port Scanner
- Hacking Tools For Mac
- How To Make Hacking Tools
- Pentest Tools For Android
- Pentest Tools Port Scanner
- Hack Tools 2019
- Hacking Tools Free Download
- Github Hacking Tools
- Pentest Tools Subdomain
- Hacking Tools For Windows
- Pentest Tools Windows
- Hack Tools 2019
- Hack Tools
- How To Install Pentest Tools In Ubuntu
- Hacking Tools 2019
- Pentest Tools List
- Pentest Tools Linux
- Hacker Tools For Windows
- Pentest Tools Tcp Port Scanner
- Hack Tool Apk
- Hacking Tools For Beginners
- Ethical Hacker Tools
- Hacking Tools Usb
- Hacker Tools Apk
- What Is Hacking Tools
- Hacking Tools 2019
- Hacking Tools 2019
- Hacking Tools Software
- Hacker
- Pentest Tools For Mac
- Hacking Tools Mac
- Hacking Tools Hardware
- Hacker Tools Free Download
- Pentest Tools Url Fuzzer
- Usb Pentest Tools
- Pentest Tools Alternative
- Android Hack Tools Github
- Hacking App
- Hacking Tools Download
- Hacking Tools Windows 10
- New Hacker Tools
- Hacker Tools For Ios
- Hack Tools Mac
- Hack Rom Tools
- Hacker Tools List
- Github Hacking Tools
- Game Hacking
- Pentest Tools Windows
- Hack Tools
- Pentest Tools Nmap
- Hacking Tools And Software
- Hacker Tools For Windows
- Hack Tools For Ubuntu